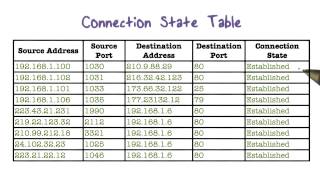
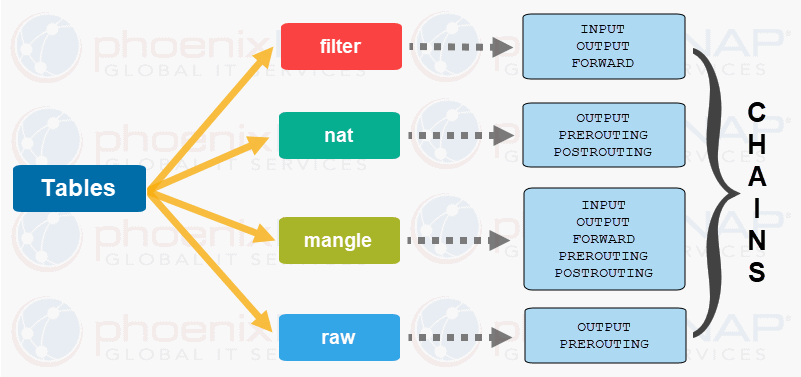
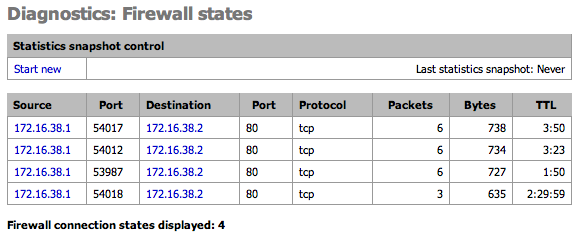
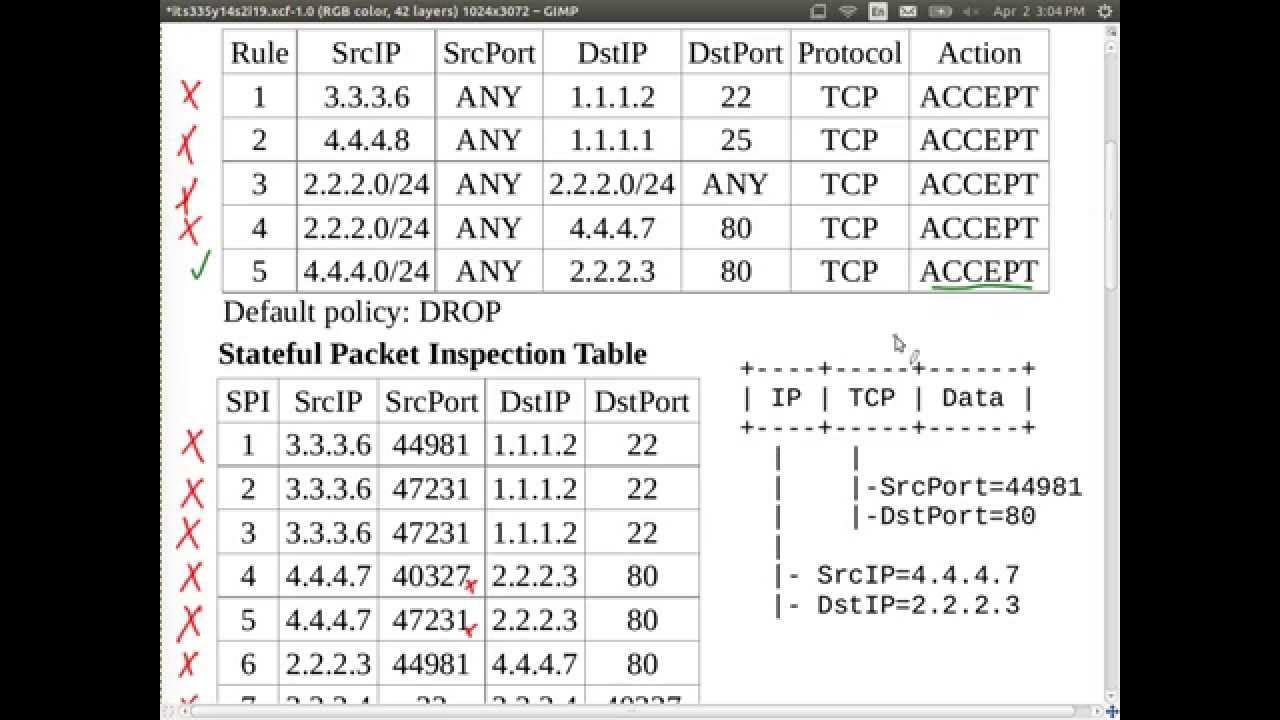
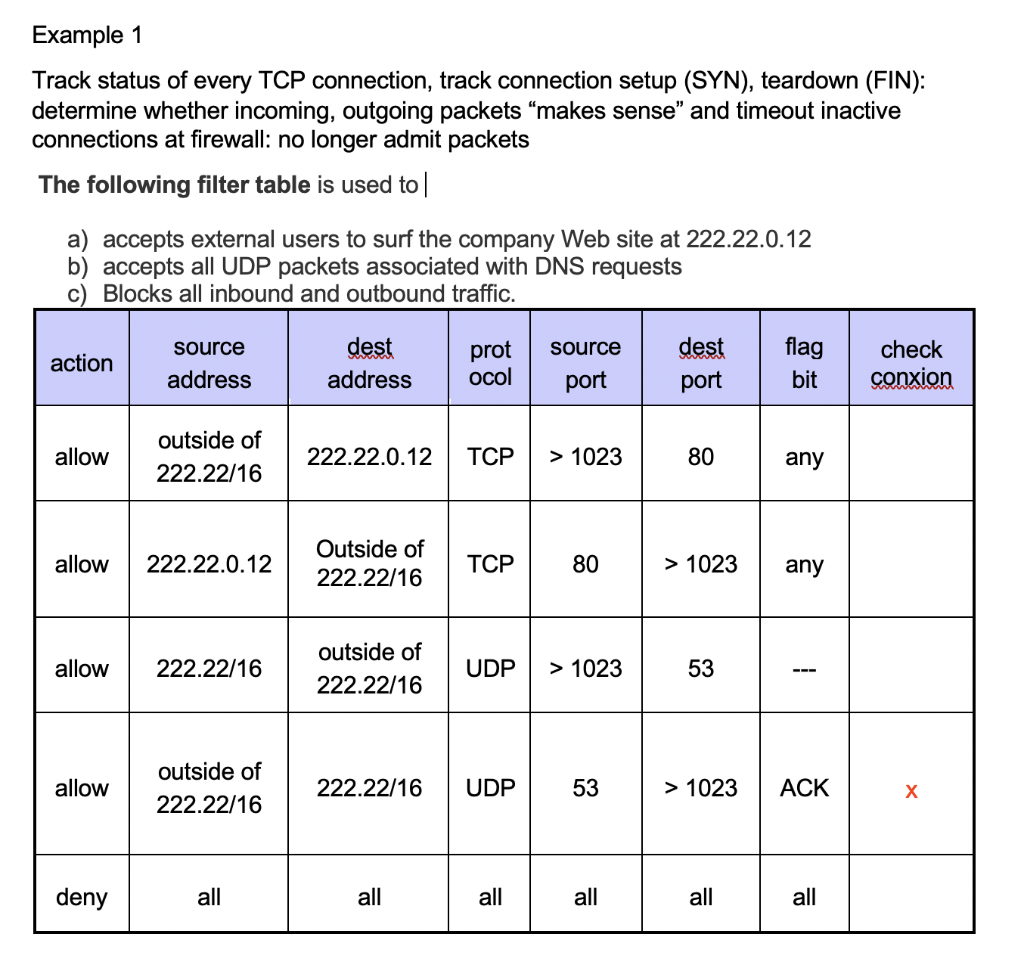
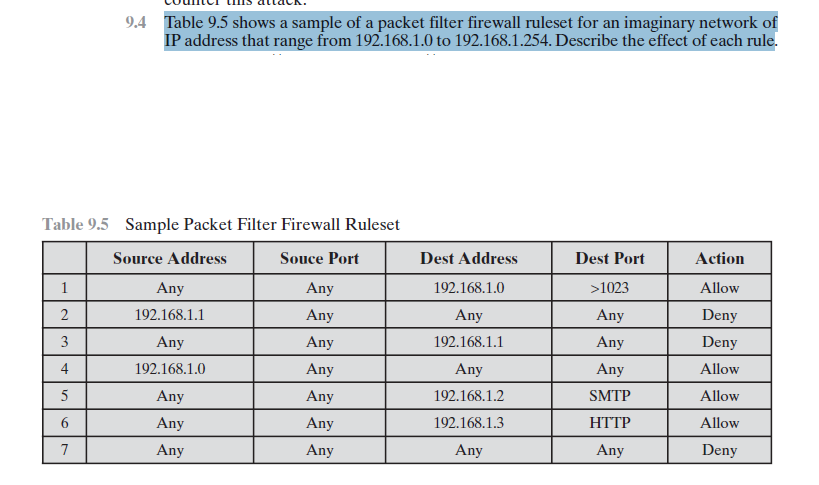
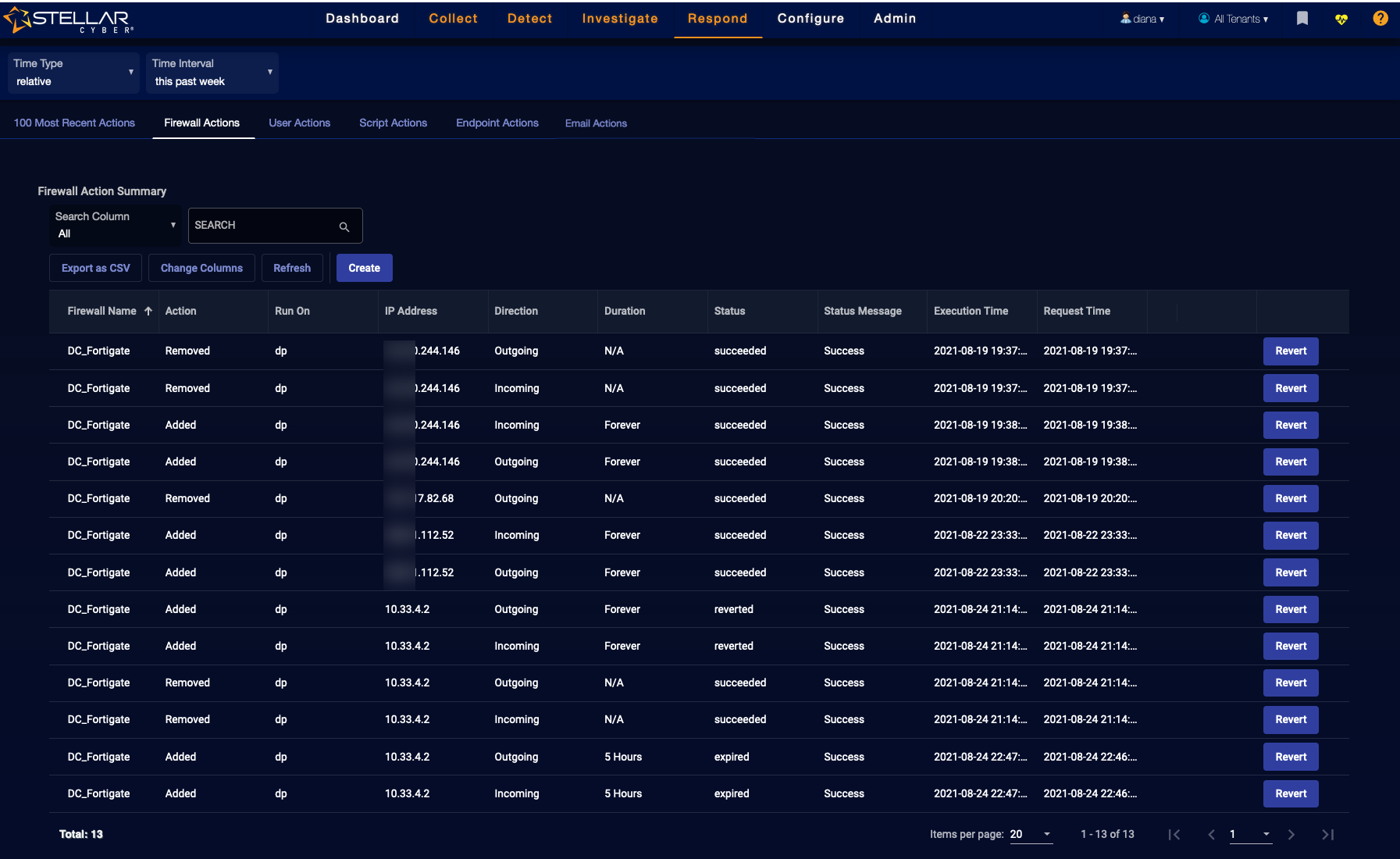
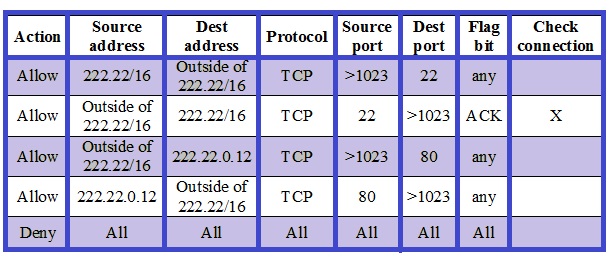
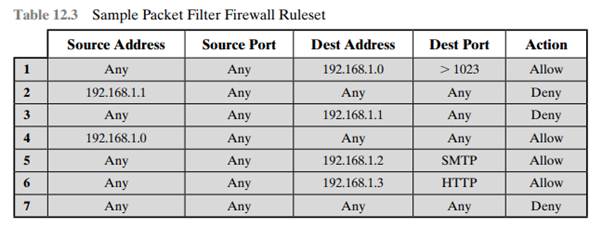
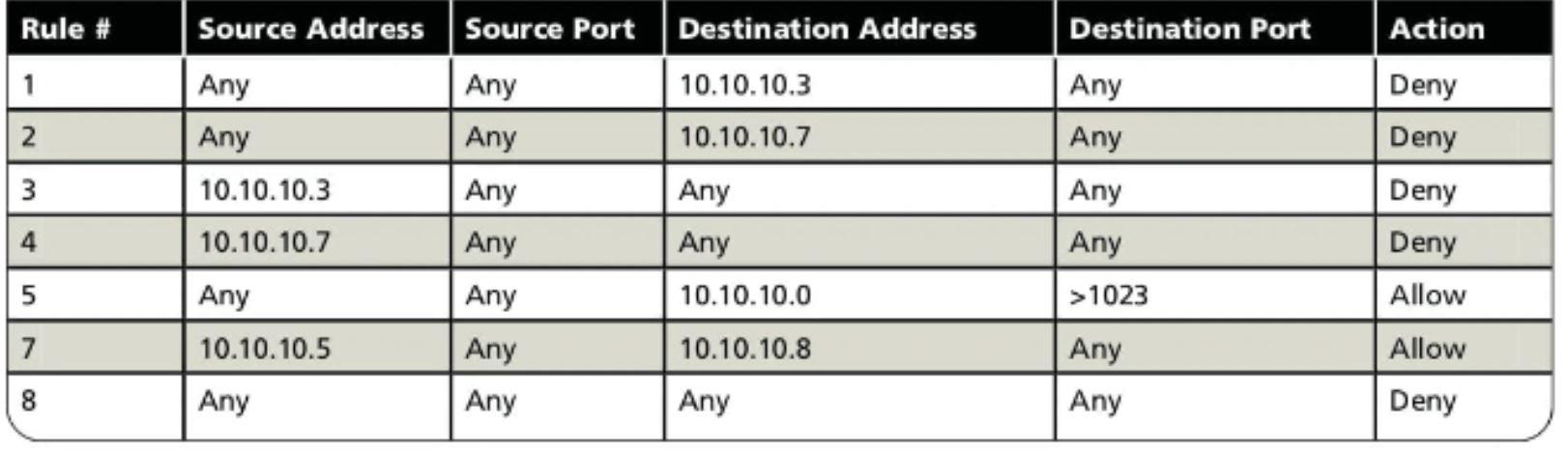
SOLVED: FIREWALL RULES The scenario describes the pertinent details of a small network, including specific addresses and port numbers. Your task is to determine if the inbound firewall rules in the table

Table 1 from Firewall Policy Diagram: Structures for Firewall Behavior Comprehension | Semantic Scholar

Table I from Automatic detection of firewall misconfigurations using firewall and network routing policies | Semantic Scholar
![PDF] Firewall Rules Analysis | Semantic Scholar PDF] Firewall Rules Analysis | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/39d214c7dc7f47a7cff4e2056c452ec470b7b996/1-Figure1-1.png)