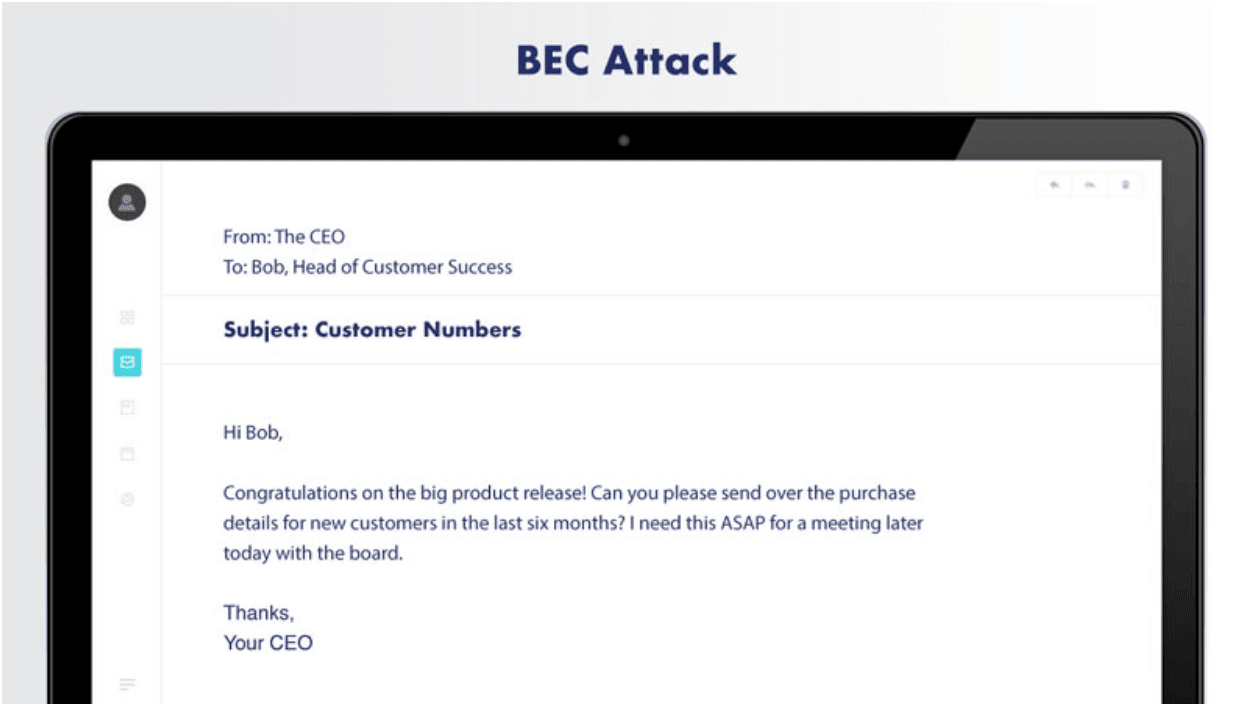
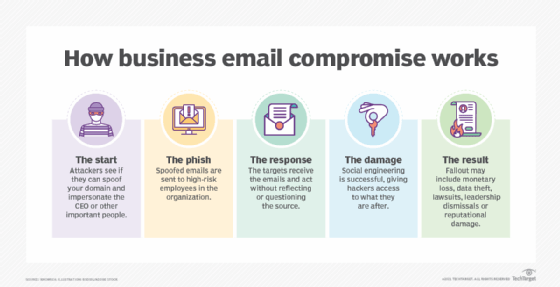
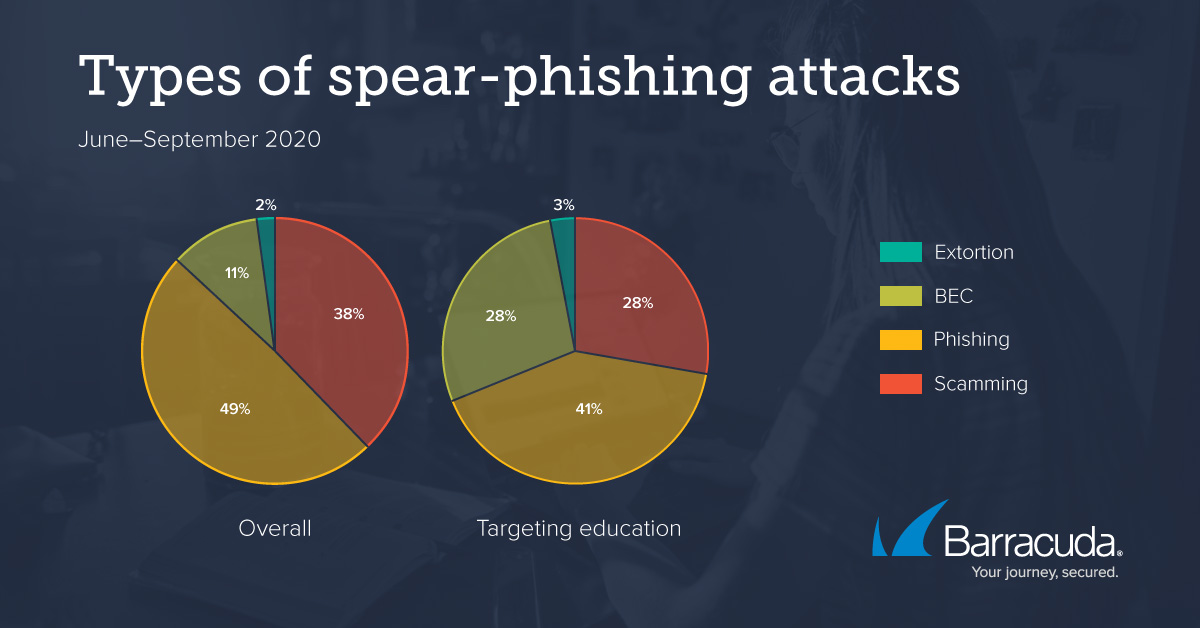
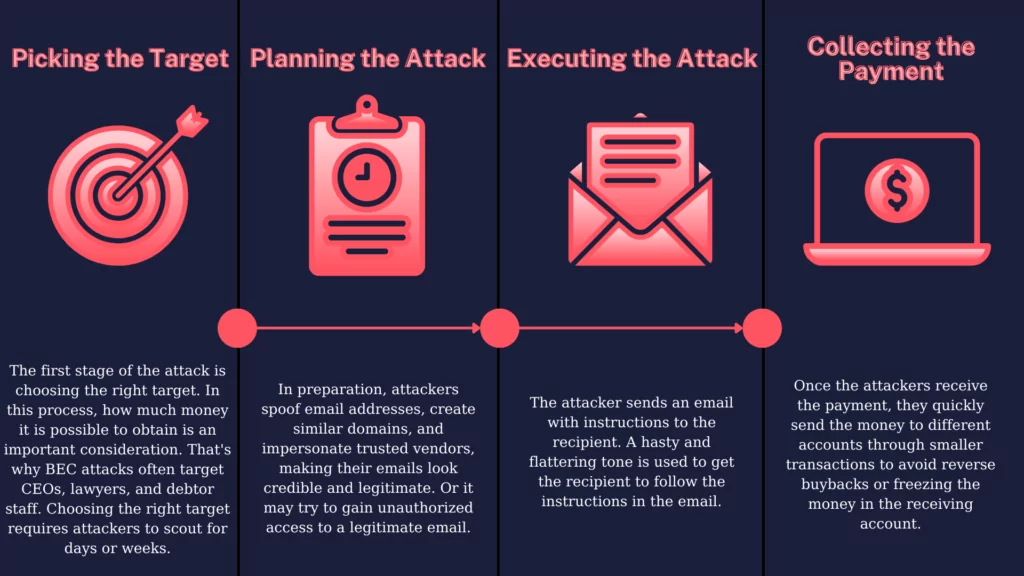
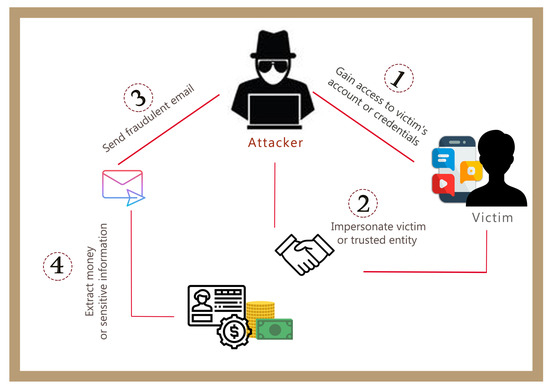
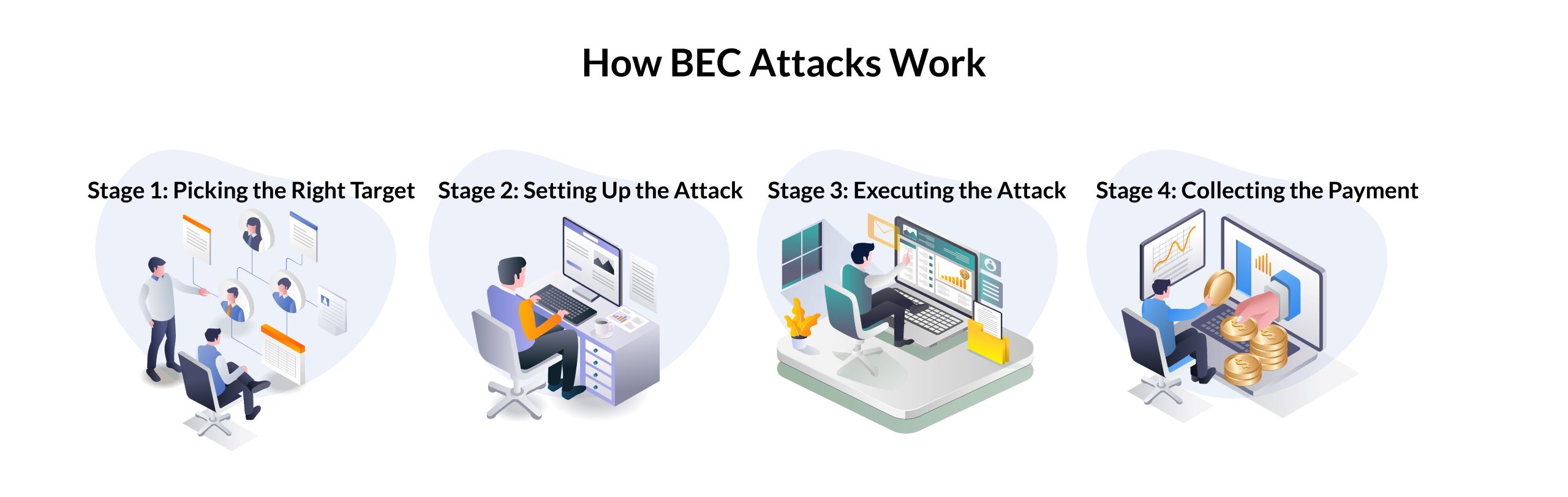
Business Email Compromise: Unmasking the Tactics Behind CEO Fraud and Prevention Strategies - Security Investigation
JCP | Free Full-Text | Business Email Compromise (BEC) Attacks: Threats, Vulnerabilities and Countermeasures—A Perspective on the Greek Landscape

Armorblox Email Security Threat Report Reveals 72% Rise in Business Email Compromise Attacks in 2022

Business Process Compromise, Business Email Compromise, and Targeted Attacks: What's the Difference? - Security News


.png)